When a cyberattack hits, the situation quickly devolves from an IT issue to a leadership crisis. Systems go down, people panic, and suddenly everyone expects you to fix it and asks “when will we be back up?” (And, how would you know?)
If you're a leader of a not-for-profit organization, you may already feel stretched thin with tasks like balancing audits, donor reporting, insurance, payroll, and compliance. You may not think of cyber security as your responsibility. But the truth is: the effectiveness of an organization’s cyber response has more to do with planning, coordination, and culture than technical skill.
And planning starts at the top.
Why Cyber Readiness Matters (Even If You’re Not a Tech Person)
Not-for-profits are increasingly being targeted with cyberattacks. Attackers assume you have weak defenses, outdated systems, and limited internal IT expertise. They’re often right.
Ransomware action over time globally:
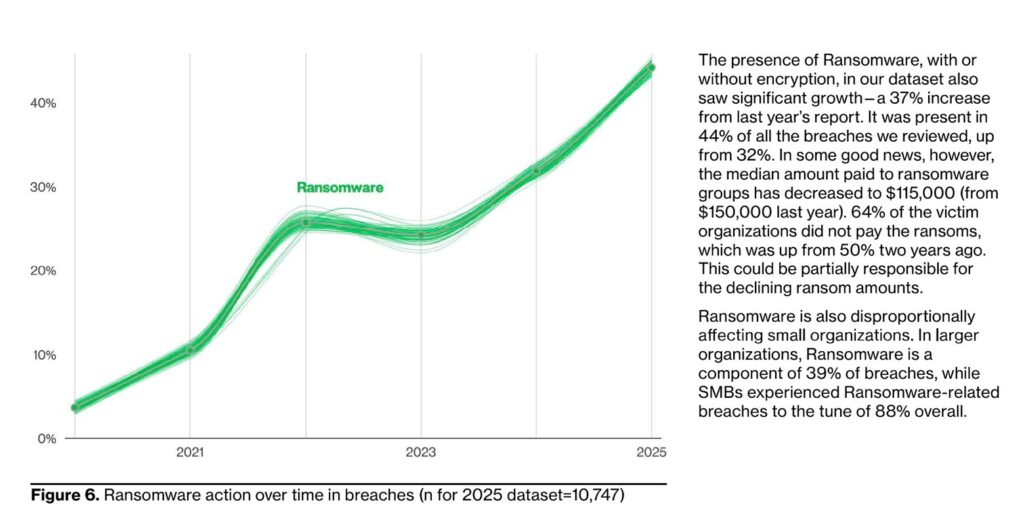
Source: Verizon 2025 Data Breach Investigations Report
Yet the stakes are just as high for your organization as they are for a corporation: donor trust, client privacy, continuity of programs, and reputation are on the line.
Cyber insurance can help with the financial fallout, but only if you have it in the first place. Many policies now require that you not only have a cyber incident readiness plan, but that you have a relatively mature IT environment and security defenses in place.
What Cyber Incident Readiness Actually Looks Like
Most cyber readiness guides are laden with jargon tuned for large enterprises or the military. Let’s skip that.
Instead, here’s a plain-English summary of what an actual response plan should include:
- Defined Roles
In a crisis, clarity beats expertise. Know ahead of time who:- Makes the call to proactively shut down systems
- Debriefs the board
- Engages your cyber insurance provider
- Handles internal staff messaging and external customer messaging
- Interfaces with PR or legal experts, if needed
Heads up: If the answer to all of those is “the IT guy,” you do not have a real plan. You have a single point of failure.
- Quick Detection
Most attackers lurk inside a network, gathering information, for 24 days before being noticed. That’s a long time to be quietly siphoning data or spreading ransomware. Ask your IT provider:- How would we detect whether we’ve been compromised?
- Can a response to suspicious activity be automated?
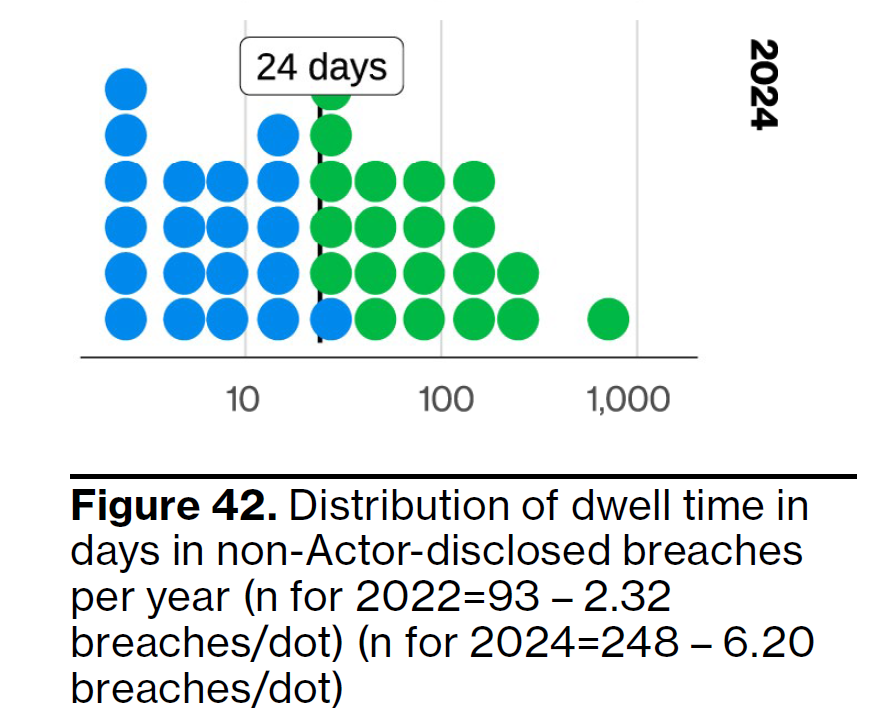
Source: Verizon 2025 Data Breach Investigations Report
- Authority to Act
If a breach occurs, seconds count. Who’s empowered to isolate systems? Who will approve vendor engagement or ransom negotiations? Who will restore data from backup? These decisions should be pre-authorized, not made on the fly, in the heat of the moment. - Tested Backups
Your backups are only useful if they work. When’s the last time someone did a full restoration of a critical system rather than just a single file? The full system. Is your data in SharePoint backed up too? - Tabletop Exercises
One of the lowest cost and highest impact ways to prepare for an incident and train a team is to host a tabletop exercise. These events are discussion-based simulations in which the team walks through a fictional incident and asks questions. It’s excellent practice and is often required by insurance carriers.
Act Now
You don’t need a 40-page policy gathering dust. You should have a one-page response flowchart and a leadership team that knows the plan, like any other safety or emergency response procedure.
Start here:
- Review your incident response plan with your executive team and IT provider.
- Identify one or two key gaps; remediate those proactively.
- Schedule a tabletop exercise. Even 45 minutes will surface critical issues.
- Connect with your cyber insurance broker and ask “What does our policy require in terms of incident readiness?”
The Bottom Line
Cyber incidents are inevitable. Panic is not.
Strong incident response isn't about having the best technology. It's about planning, assigning roles, rehearsing, and staying calm under pressure. That’s not an IT function; it is an organizational leadership function.
How Kreischer Miller Can Help Your Not-for-Profit Organization Develop a Cyber Incident Readiness Plan
Kreischer Miller’s Incident Response Process:
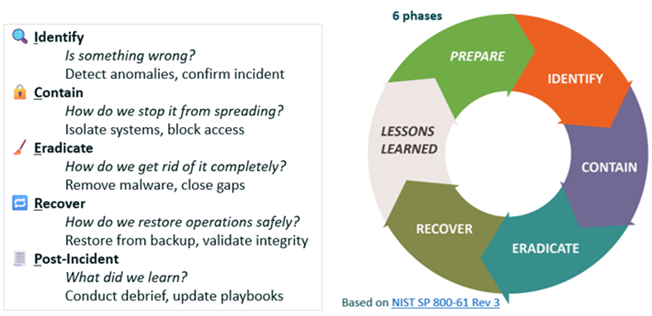
Don’t wait until something breaks to figure out who’s in charge. Plan now, and you’ll sleep better knowing that when (not if) something goes wrong, your team will know exactly what to do.
If you would like to discuss the next steps as you begin planning, please contact us. Our Technology Solutions Group can assist with your incident response plan and schedule your tabletop exercise.
If you would like to learn more about cyber incident readiness, check out the rebroadcast from this recent webinar co-hosted by Kreischer Miller and Tech Impact.

